- Resources
- Application Stories
- A Nuanced Approach to C-UAV Technology
Clear Skies, Minimal Turbulence
A Nuanced Approach to C-UAV Technology

Overview
In recent years, the increased accessibility of commercial off-the-shelf (COTS) drones has rapidly changed the nature of their use. Previously tools reserved for large organizations and governments, drones (or Unmanned Aerial Vehicles (UAVs are now consumer products with tangible commercial potential. With this has come great benefits. In fact, the use of UAVs has made it easier than ever to carry out important work such as environmental surveying and infrastructure inspection. Moreover, UAVs have been broadly adopted as part of search and rescue procedures by emergency services worldwide.
As with any new technology however, there are pitfalls to this rise in accessibility, particularly as it pertains to security. For example, while the majority of commercial UAVs are used in a safe manner, they also have the potential to disrupt critical infrastructure such as airports. Examples of this have been seen in multiple high-profile runway closures, flight cancellations, and near-misses across the world as a result of UAV activity in zones that rely on precise, uninterrupted communication channels.
Recognizing the need for a Counter-Unmanned Aerial Vehicle (C-UAV) system that balanced the need for effective mitigation with minimal disruption to other systems, one company used AAEON’s EPIC-TGH7 to develop a more nuanced application.
The Need for a Goldilocks Solution
There are a number of considerations that need to be made when deploying C-UAV systems. Chief among these is the suitability of the system’s underlying technologies to the environment it operates in. It is for this reason that a multilayered approach integrating a range of technologies to identify and mitigate UAVs is recommended. Some common technologies for identifying and mitigating unauthorized UAVs include:
Radar
Radar emits radio waves that measure the reflections off objects within its scope. This allows users to track the location, distance, speed, and trajectory of UAVs.
Radio Frequency (RF) Scanning
Scans large areas for the communication protocols used by UAVs, allowing differentiation between authorized and unauthorized UAVs based on its unique RF characteristics.
Radio Frequency (RF) Jamming
Involves emitting RF signals on the same frequency as an unauthorized UAV, which serves to disrupt the communication and navigation signals in place between the UAV and its operator.
GPS Spoofing
GPS spoofing sends fake GPS signals to unauthorized UAVs in order to mislead its GPS receiver. As a result, unauthorized UAVs are unable to accurately traverse the restricted zone and cause it to land or return to a designated ‘home’ location. A challenge with using this method in an airport-based C-UAV system is that it risks interfering with navigation systems used by authorized UAVs and aircraft.
Kinetic UAV Mitigation
Relies on physical countermeasures. Examples include the use of High-Power Microwave (HPM) Systems and drone capture systems. HPMs render UAVs inoperable by sending electrical currents that overload voltage-sensitive components. Meanwhile, capture systems use propelled nets to physically capture UAVs. Both of these methods raise safety issues, with the risk of debris falling being a major concern.
Building an Airport-Friendly C-UAV Solution
To overcome the challenges associated with employing existing C-UAV methods outlined above, AAEON’s customer developed a new method of mitigating UAVs in restricted zones.
While the company’s system would use passive UAV detection methods such as radar scanning and RF detection, its objective was to pair them with a more nuanced form of UAV mitigation – protocol manipulation. This mitigation strategy differs from RF jamming, GPS spoofing, and kinetic UAV mitigation by instead using dedicated RF transmitters to monitor and decode the radio transmission structure between detected UAVs and their controllers through vulnerabilities in commercial UAV communication protocols.
By employing protocol manipulation, the application would be able to gain access to data such as the UAV’s make, model, and serial number, as well as the last known location of its controller. Effectively taking over the radio link between the UAV and its controller, the application could subsequently send takeover or command injection signals to the UAV, such as forcing it to ‘return to home’ or safely land at a predetermined location.
Project Launch Pad: AAEON’s EPIC-TGH7
The prerequisites for the central component of the customer’s C-UAV system not only related to its ability to host various sensors, but to have sufficient compute power to process data received from them. Moreover, the solution needed to support fast data exchange to reduce the total time required to identify, track, and implement control instructions to initiate UAV mitigation.
The customer ultimately chose AAEON’s EPIC-TGH7 as the central hardware component for their C-UAV solution, noting the single-board’s balance between performance, ruggedness, and connectivity.
High-Powered Intel Xeon Processing
Equipped with the 45W Intel® Xeon® W-11865MRE Processor, the EPIC-TGH7 offered 8 cores and 16 threads of processing power, which was more than enough to handle data streams from multiple RF receivers and radar sensors.
The platform also provided a number of on-chip technologies such as Intel® AVX2 and Intel® AVX-512, which facilitated the processing of multiple digital signals, helping to decode modulation schemes to extract structured data such as serial numbers from raw bitstreams. This data subsequently assisted the application in analyzing the radio transmission structure between the UAV and its controller, allowing it to discriminate between authorized and unauthorized UAV.
The board’s Intel® Xeon® W-11865MRE Processor also offered high clock-speeds and parallel processing capabilities, compounding the efficiency with which it exchanged data with the NVMe module hosted by the EPIC-TGH7's M.2 2280 M-Key. Such a setup allowed for NVMe commands to be sent over PCIe to the SSD’s controller directly from the CPU, dramatically reducing latency when executing high-throughput tasks like capturing raw RF signals, storing UAV identification metadata, and logging high-resolution sensor feeds.
Custom Quad LAN Interface
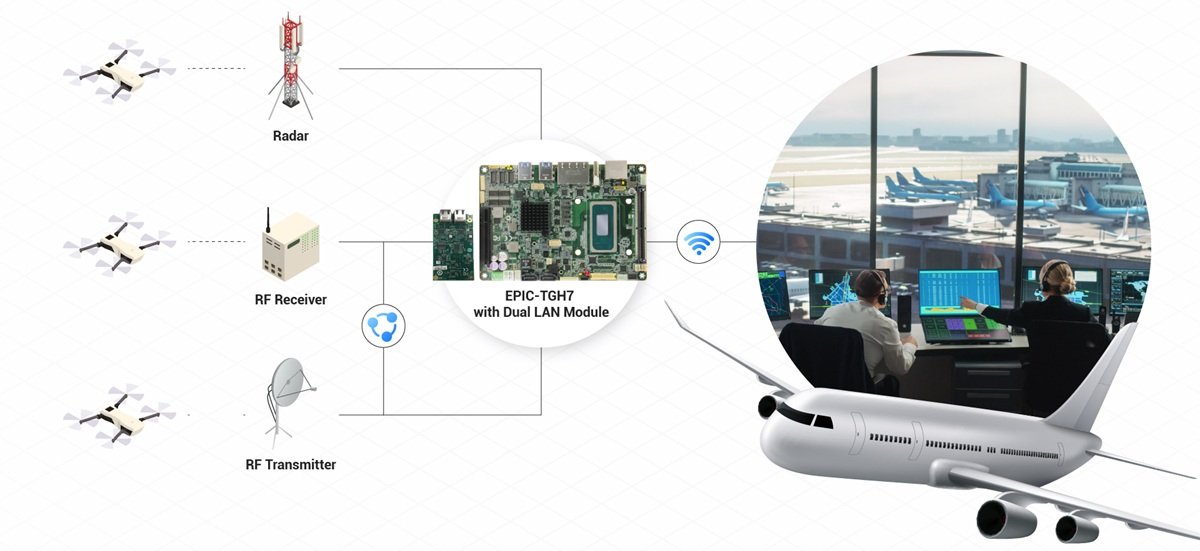
To acquire data, the customer leveraged the EPIC-TGH7's two onboard LAN ports for RF receiver and radar sensors. However, given the application’s need for dedicated RF transmitters, additional connectivity was required. As such, the customer took advantage of AAEON’s world-class customization services, integrating a dual-LAN module via the board’s FPC connector. This granted them two additional LAN ports, with one hosting an RF transmitter and the other an additional sensor.
With multiple different sensors all transmitting various data metrics to the EPIC-TGH7's, synchronization was paramount. Fortunately, the board provided dedicated drivers for both the Intel® Ethernet Controller I226-IT and Intel® Ethernet Connection I219-LM PHYs. As a result, the customer’s application could take advantage of native support for IEEE 1588 Precision Time Protocol (PTP) to implement time synchronization across sensors to synchronize timestamps across geographically separated receivers.
Dynamic Expansion
The customer’s C-UAV application’s primary functions of identifying and mitigating unauthorized UAVs were executed locally, meaning the system is able to operate autonomously. However, secure communication between the ground and central command centers is vital, particularly when used in commercial airports.
To provide the application with this additional connectivity, the customer made use of the EPIC-TGH7's broad expansion options. The board’s M.2 3052 B-Key and mPCIe slot were populated with an LTE and Wi-Fi module, respectively. This gave the EPIC-TGH7 two wireless interfaces through which to communicate with other components of the C-UAV application. In practice, the LTE module was primarily used to relay drone serial numbers, GPS positions, and threat alerts to the airport’s central command center in real-time. Meanwhile, its Wi-Fi functionality was useful in the context of distributed sensor networks where multiple systems could share detection data over a Wi-Fi mesh.
Application Architecture
The Outcome – A Multilayered, Safer C-UAV System for Commercial Settings

The customer’s application is not unique in the technology it utilizes to identify unauthorized UAVs in restricted zones. However, it does stand out in its approach to UAV mitigation. By leveraging the processing capabilities, agile expansion, and flexible interfaces offered by the EPIC-TGH7, the customer was able to implement protocol manipulation that allowed the application to take over command of unauthorized UAVs and safely remove them.
This approach not only offered the tangible benefit of protecting commercial airports from unauthorized UAVs, but increased the opportunity for forensic analysis to take place by extracting key information about the UAVs it encountered. Such intelligence has the potential not only to help law enforcement trace those responsible for UAV misuse, but also to deter others.
Most importantly, this application illustrated that C-UAV systems can be safely used in critical environments such as airports without causing operational disruption. In this respect, the application serves to both boost security and safety, but also incentivize proactive measures from a business perspective, as the impact of service disruptions can be truly damaging to airports, both financially and when it comes to maintaining public trust.





