- Resources
- White Papers
- AAEON’s Multilayered Software Security Framework

NOW AVAILABLE ON...
The Added Vulnerability of Running AI Algorithms on the Edge
The shift from cloud-based to edge AI operation has changed how critical application data is accessed, increasing the surface area of threats like firmware injection and man-in-the-middle attacks due to the lack of physical security offered by edge AI devices when compared to centralized data centers.
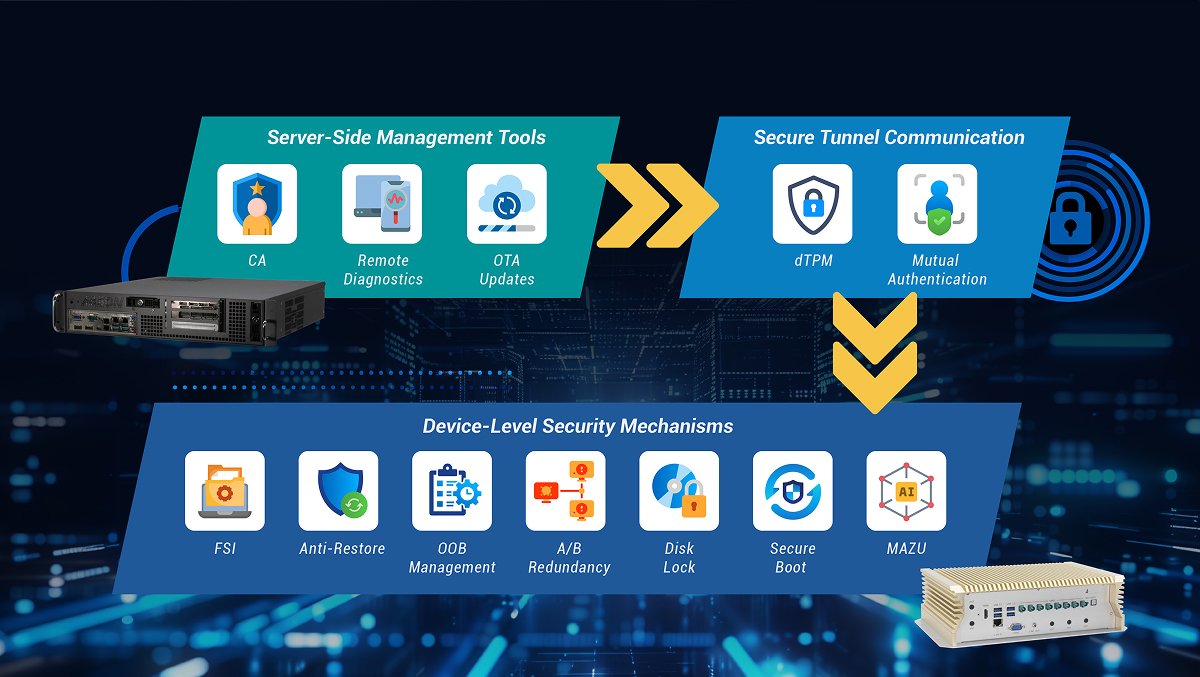
Recognizing the need for a more comprehensive solution, AAEON has developed a multilayered software security framework designed to address security threats throughout each level of the AI application ecosystem. This framework includes server-side management tools, device-level security mechanisms, and secure tunnel communication protocols, all working in concert to maintain the integrity of critical edge AI application data. This package includes AAEON's tailored Trusted Execution Environment (TEE) for AI model protection, MAZU, which is now available on the BOXER-8621AI, BOXER-8641AI-Plus, and the BOXER-8651AI-Plus, with expansion to additional products from AAEON's Embedded AI System range to follow.
Discover how AAEON’s three-layer security framework protects your AI assets across every level of your deployment ecosystem.
Understanding the Risks of Edge AI
Increased Threat Exposure

Although deploying AI on the edge is a performance game-changer, it also expands the attack surface available to hackers due to edge devices' physical exposure and decentralized placement within broader application ecosystems.
AI Algorithms as Business Assets

The leaps made in the sophistication of edge computing architecture have made it so proprietary AI models on deployed on edge devices are attractive targets for cyberattacks, particularly with respect to highly regulated sectors.
Evolving Cyberattacking Tools

The methods used by hackers have grown more sophisticated, and traditional cloud-based security frameworks do not adequately address the unique threats that are faced by edge devices when deployed as part of a multifaceted application ecosystem.
Understand the Risks, Explore the Tools, and Secure Critical Edge AI Data
What’s Inside?

Threat Mapping
A breakdown of the key areas of vulnerability within edge AI application structures.
Three-Layer Defense Strategy
A detailed blueprint of the protection offered by AAEON’s comprehensive software security framework.
Tech Deep Dive
An overview of key security framework components such as server-side management tools, device-level security mechanisms, and secure tunnel communication protocols
Actionable Insights
How you can utilize AAEON’s proprietary security framework across its edge AI platforms to future-proof your AI deployment from day one.
Ready to Fortify Your Edge AI Infrastructure?
No matter which sector you operate in, application data such as AI models, inference data, and proprietary algorithms require protection. AAEON’s new white paper is the go-to resource for navigating edge security in a decentralized world.
Download for free and start building intelligent AI applications, smarter.









